Wikipedia commons
Once upon a time, if a thug wanted to take your money, he pretty much had to be close enough to hold a gun on you. Not anymore. These days, somebody halfway around the world can steal from you. Estimates of the size of the global criminal economy approach $1 trillion a year, or roughly 1.5 percent of global GDP. There are a lot of people in the world who make their livings from crime. If we’re not careful, we’ll end up as their victims.
A couple of recent scrapes with the criminal economy have reminded me of just how vulnerable all of us are, assuming that we have a computer, a cell phone, a bank account, and credit cards or debit cards. Don’t we all?
Increasingly, criminals try to reach you through your cell phone. Long ago I stopped answering calls from unknown callers outside my area code. Just yesterday a scammer with an 855 area code left this voice mail:
“Hello, I’m calling in regards to a formal complaint that’s been filed against [name of friend in California]. If you have any information that can lead to the whereabouts of this individual, please contact us at 855-207-2381. Again, 855-207-2381 or press any key on your dial pad to be connected immediately. Our next step will be filing the necessary paperwork with the local county court. Thank you for your cooperation.”
I had heard of this scam before, so all I did was alert my friend in California. His mother and sister had received similar calls. How did the scammer get my telephone number? I’ll never know. One possibility is that malware on my friend’s computer or cell phone compromised his address list. But what’s troubling about this particular scam, though, is that it generally targets people who have had previous minor scrapes with the law, so it’s easy to believe that that person is in trouble again. I suspect that the scammers are scouring public records. About 12 years ago, I had posted bail for this person after he was arrested for an unwise altercation with a parking lot attendant. My name would appear in the court documents, which are public record. The scam, I understand, is to try to get someone to send them money to drop a charge, though there is no charge.
A few months ago, I took responsibility for maintaining the web site for the Democratic Party in my county. The web site had been hacked a few months earlier and needed to be cleaned up. I did the cleanup work, rebuilt the web site, and went through the onerous process of getting Google to remove the dreaded “This site may be hacked” line in Google searches. About two months later, in spite of some extra security precautions, the web site was hacked again. I cleaned it up again. That very night, it was hacked a third time. Criminals use this kind of web site hacking to build their “bot” networks. Hijacked web sites can be used to distribute malware, to send spam, to market illegal products, or even to host illegal forms of porn.
I certainly am not boasting, but this web site and blog have never been hacked. Though I have taken every precaution I know how to take to secure this web site against hackers, constant vigilance is required. That takes time. The security logs for this blog show that it is regularly under attack. I recently added the ability to block access to this blog to most countries outside North America and Europe. Until I started that country blocking, most of the hacker probes came from Russia, Ukraine, and Asia.
There are three categories of global crime to which most of us vulnerable: Identity theft, online risks such as malware, and credit card fraud.
I’m no stranger to identity theft. Some years ago when I was living in San Francisco, someone using my name and Social Security number got a telephone in San Jose and ran up a bill that they never paid. Believe it or not, the law required that I prove to the telephone company that I didn’t do it, as opposed to the telephone company having to prove that I did. You can imagine how much time and aggravation that cost.
Secure banking
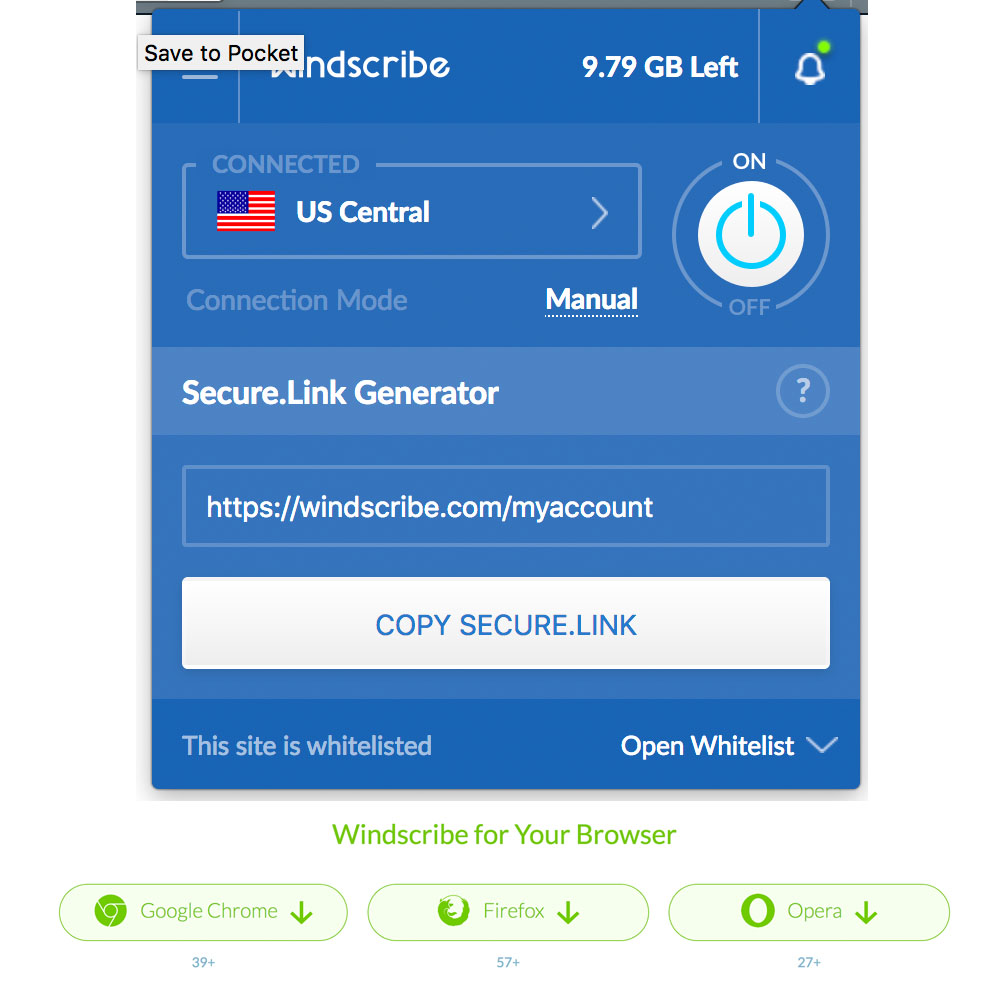
If you’re concerned about identity theft, online security risks, and Internet privacy (we all should be), then I’d recommend that you do some Googling and reading on precautions that you can take. A good place to start is the Electronic Frontier Foundation: https://ssd.eff.org/
However, I do want to talk a bit about secure banking.
For 25 years, I have been using the same account with Bank of America. When I opened the account, I had just moved to San Francisco, and Bank of America was a San Francisco hometown bank. Some years later, after an ugly buyout, Bank of America moved its headquarters to Charlotte. It’s now a big bank, and a mean one. But I have kept my Bank of America account because the bank has never been mean to me personally and has never charged me a cent. Bank of America also has some of the best security of any bank. Twice in the past, someone has made fraudulent charges using my debit card number. In both cases, the bank immediately detected the fraud, alerted me with phone calls and text messages, cleared the fraudulent charges, and sent me a new debit card.
For years, I’ve paid my bills online using Bank of America. Almost all my spending went through my debit card. I carry very little cash. Though I did not need a credit card, Bank of America kept tempting me with a credit card with “cash back” benefits. You get 1 percent on all purchases, 2 percent at grocery stores and wholesale stores, and 3 percent at gas stations. That would add up to a few hundred dollars a year for me. But what really sold me was a feature that was not available with my debit card. It’s the ability to create temporary “virtual” credit card numbers for online purchases. You assign enough money to the virtual card to cover the purchase. The virtual card expires in a month or two. And the online merchant never knows your real credit card number. I now use virtual credit cards for all online transactions, and I “locked” my debit card, which I still have, to block transactions. I can “unlock” the debit card any time from my computer or cell phone. Another free benefit that came with the credit card is a free monthly credit report. All in all, I think this is a pretty good deal. Bank of America is giving customers the ability to protect themselves, which also protects the bank. And as long as you pay your bill in full at the end of the month, there are no charges for the card, and you get “cash back.”
Don’t lose things!
A couple of months ago, on a trip to Asheville, I thought I had lost my wallet. It turned out that I had not lost it. Rather, while riding in a friend’s vehicle, my wallet had fallen through the crack between the seat and the console when I had awkwardly gotten my wallet out to pay us out of a parking deck. But in the three-hour period in which I thought my wallet was lost, I realized what a pain in the neck it would be to lose it. That would be an invitation to identity theft, and all one’s cards would have to be quickly canceled and replaced. Precaution: Make a copy of everything important that you carry with you so that you know whom to call and what has to be replaced.
Where is law enforcement?
As far as I can tell, almost no one ever gets arrested and prosecuted for online crime. Criminals now routinely ignore do-not-call lists, etc., and they get away with it. We spend untold billions of dollars on the low-level threats (more rare than lightning strikes) that are hyped in the media, such as the threat of terrorism. The political class have been worse than useless in taking a rational approach. Instead, for political gain, they hype non-existent threats such as transsexuals in bathrooms and do next to nothing to defend us against these new forms of global crime. We’re on our own.
Living off the grid and leaving no digital trail is a wonderful fantasy, but almost no one can pull it off. Corporations and governments know a heck of a lot about us. All we can do is try to prevent information about us from falling into the hands of the criminal economy.