Two Bambis (white spots and all) came wandering out of the woods behind Acorn Abbey at dusk this evening to steal my clover. I did not see their mother, but I doubt that she was far away. The photo is blurry because the light was poor. The photo was taken through a window of Acorn Abbey. Notice how dark the woods are under the canopy.
Almost as green as Ireland
I was expecting a miserably hot, dry August. But instead we’ve had a long run of rainy weather. About 7 inches of rain has fallen here in the last nine days. Everything is emerald green. The cloudy weather has held the temperatures down. The high for today was about 77. The meadows are boggy, just like Irish meadows. We’ve had several flash flood watches, but so far no serious flooding.
All these photos were taken in the Dodgetown area about 3 miles from Acorn Abbey.
Defending your privacy on the Web
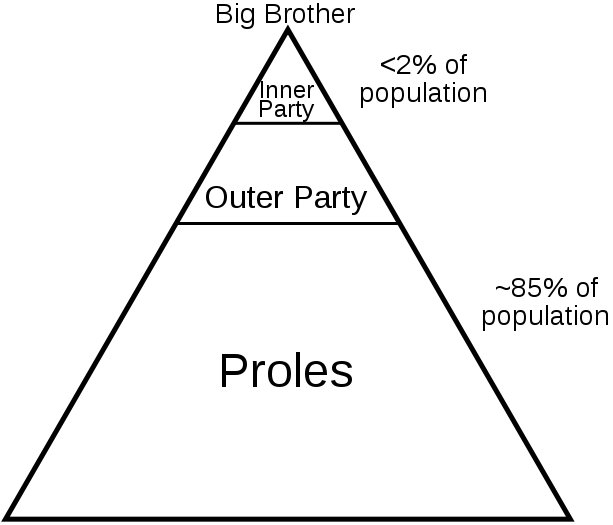
The social and political classes in George Orwell’s novel 1984
We’ve all been told that there is no such thing as privacy on the Web. That is true. Still, we are not helpless. Recently I got quite angry after I learned about a whole new category of privacy threat on the Internet — shady private organizations that collect data on you and then give it, or sell it, to the government. Glenn Greenwald posted an article on this a couple of weeks ago.
This motivated me to put a little time and research into figuring out how to attain a reasonable level of privacy on the Web with a reasonable effort. I was not interested in what I’d call a paranoid level of privacy. That would take a great deal of effort and would make it much harder, and less fun, to use the Internet. But surely, I thought, there is a reasonable level of defense that anyone could achieve with a little study and some changes in how you set things up on your computer.
There are three broad categories of privacy and security risk on the Internet:
1. Illegal activity. This would include password “phishing” scams, spyware, viruses that take over your computer and turn it into a “bot” under the control of spammers, etc.
2. Activity that is legal but extremely intrusive. This includes efforts to track you and identify you on the Internet, the better to target ads to you or to sell you something. This is extremely common, and it’s getting worse.
3. Tracking aimed at the ability to build dossiers on millions of Americans, names and all, that can be sold to the government or otherwise used against you. It was this type of activity that Greenwald (Greenwald is a Constitutional lawyer) was writing about in the link I posted above.
For category 1, your best defense is to keep your computer up to date with security fixes of the type that are regularly released by Microsoft and Apple.
For categories 2 and 3, there is much you can do to defend yourself by making some changes in how your configure your computer.
I’m going to list some steps that I took — and that you can take — with a brief description of the privacy threat and how the threat can be reduced. Please appreciate that I can’t answer questions about how to make these changes on your computer. Instead, you should do your own research and learn about how to manage these things. Then you’re on your way to empowering your own self defense.
1. Use two browsers. One of the ways that snoops can figure out your identity is to snitch your identity from sites that you sign into. I am particularly wary of Yahoo, Facebook, and Google. If you are signed into them, they know who you are. Clever tracking cookies can then identity you by name on other sites. For example, recently the Washington Post’s web page started displaying a new feature that shows (among other things) what you and your friends on Facebook have been reading on the Washington Post web site. The Washington Post was quick to put out a disclaimer about why this is no threat to your privacy. You decide. As far as I’m concerned, it’s yet another reason to ignore the Washington Post, which (to my judgment) is no longer a real newspaper but merely a mouthpiece for the Washington establishment.
So here’s what I did. I use a Macintosh, and my regular browser is Safari. I downloaded Google Chrome to use as a second browser. One browser is my “identity” browser, and the other is my “no-identity” browser. When I sign in to Facebook, I do that in the “identity” browser, Google Chrome. But I don’t go anywhere else in that browser. Someone could glean my identity from Facebook and track me all day, but they’d only discover that I didn’t go anywhere but Facebook.
I do the rest of my browsing in Safari. But when browsing in Safari, I never sign in anywhere. The other important step is to delete all your cookies. Now, cookies may do a couple of things for you that you like, like enable a web site to remember that you’ve been there before. But it’s actually pretty easy to browse happily without those minor conveniences that cookies can give. Mostly, cookies are there to support the business models of the web sites you visit, whether legitimate or snoopy. But I don’t care about anyone’s business model on the web. I care much more about my privacy. Delete your cookies frequently, even once a day. If you haven’t looked at your cookies in a while, you may be stunned to find that you have thousands of them. Cookies are being used more and more, and mostly they are being used against you.
2. Use a DNS other than your internet service provider’s DNS. I cannot explain here what DNS is or tell you how to change your computer’s DNS settings. You must do your own research and understand it well enough to make this change for yourself. My ISP is Verizon. But that doesn’t mean I have to use Verizon’s DNS. I use Google’s free, public DNS. Though I am increasingly suspicious of Google’s commitment to privacy, their written privacy policy for their public DNS does explicitly say that they won’t match your DNS lookups with other data that Google may have about you. They also say that they destroy their DNS logs on a regular basis. Based on what I know at this time, I’d rather have my DNS data logged at Google rather than Verizon. And besides, Google’s DNS service is better than Verizon’s. Here is a link to information on Google’s public DNS.
3. Get Adobe Flash under control. I’ve mentioned previously how Adobe Flash has become one of the most obnoxious players on the web. It’s for good reason that Apple’s Steve Jobs is doing battle with Adobe over Flash. Flash eats your bandwidth with unwanted fancy ads. It eats up your computer’s processing power, and, if you’re on a laptop or a handheld, will run down your battery quickly. Even worse, Adobe Flash operates totally outside of your browser’s security features. Flash’s default security settings are wide open. By default, Flash can set its own “Flash cookies,” which are much harder to find and delete because your browser doesn’t know about them. Flash permits web sites to store data on your computer. Flash even may permit some web sites to use your internet bandwidth for “peer assisted networks.” My guess is that, 10 years ago, Flash already had everything that is of interest to you as a web user. Their development effort, clearly, is focused on giving advertisers and the operators of web sites the tools they want to track users, gather data on users, and focus advertising on users. I don’t care about any company’s revenue. I care more about my privacy. So I took these steps:
a. Get a Flash blocker plug-in. For Safari, I use ClickToFlash. There are different Flash blockers for other browsers. Do some Googling for “flash blocker” plus the name of your browser, and you’ll find a way to keep Flash from running in your browser unless you explicitly give it permission.
b. Delete your Flash cookies. You may have hundreds or thousands of them. On the Macintosh, you can find them in the file system at ~/Library/Preferences/Macromedia/Flash Player/#SharedObjects. Drag them all to the trash. They are not benefiting you in any way. They are only benefiting someone’s revenue model. If you use a computer other than a Mac, Google for “flash cookies” or “flash shared objects” and see if you can’t find some instructions. Remember, I can’t help you with this. I’m only suggesting that it’s something you might want to research for yourself.
c. Change the default settings of Flash on your computer. To do this, you must go to Adobe’s web site. Lock it up as tight as possible. None of those features benefit you in any way. They all benefit those who want to track you or make money off you. I believe that Adobe intentionally makes it difficult to change the privacy and security settings in Flash. Adobe is one of the meanest players on the web today. They do not deserve our support.
4. Use a proxy service. Using a proxy service full time, at least in my judgment based on what we know at this time, is probably more trouble than it’s worth. Still, if I wanted to do something on the web that might be considered suspicious or that I think might attract attention (for example, visiting the WikiLeaks web site), then I would use a proxy service temporarily. Again, you must do your own research, but proxify.com is a good place to start.
Good luck and happy browsing. And please remember, I can’t answer questions or help you make these changes on your computer. I’d rather see you empowered to handle your own self-defense on the Internet. It’s a jungle.
Here come the hurricanes?
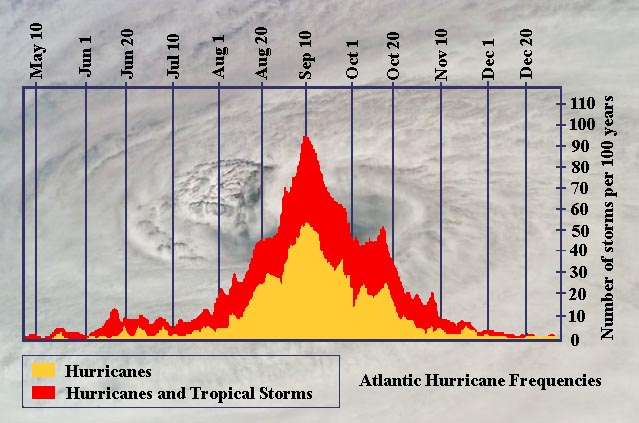
Statistically, the chances of an Atlantic hurricane rise rapidly around Aug. 18. The odds peak around Sept. 10 and remain high through mid-October.
If you’re a weather nerd, as I am, a great source of expert commentary on the weather is Jeff Masters’ blog at Weather Underground. During hurricane season, Masters posts pretty much every day. He explains what’s going on in the hurricane birthing grounds in the South Atlantic, and he tracks any developing storms.
Since I am safely situated 200 miles from the Atlantic, I’m hoping for a good, rainy hurricane season this year to help recharge the ground-water aquifer, which has not really recovered in this area from the severe drought of 2003.
A good year for butterflies
Butterflies on the milkweed behind Acorn Abbey
I’ve seen a lot of butterflies this year, particularly monarch butterflies. The presence of monarch butterflies is a good indicator on the health and variety of the local ecosystem. The life cycle of monarch butterflies is dependent on milkweed.
Though I wish I had more milkweed here, there is a very fine milkweed plant behind Acorn Abbey, near the edge of the woods. I’m sure there will be more in future years. Though I broke down and mowed my grass this year, still there are lots of wild spots and hedges where the native species can volunteer and grow as they please. I think these wild areas are very helpful to the animal and insect population.
Apple economics
If you want good apples, the best way is to grow them yourself, I’m sure. But my young apples trees probably won’t produce for two more years or so. The summer heat is hard on the appetite and the urge to cook. I haven’t made sourdough bread for over a month. But the craving for apple pie never goes away, and I expect the craving for apple pie to get even worse as fall approaches.
Anywhere in the country one drives during the summer, one sees old apple trees hanging full of apples, but how to get them? I fantasize about an apple raid. In the local grocery stores, all the apples are from Washington. All of them. The same thing is true at Whole Foods in Winston-Salem — nothing but Washington apples. I refuse to buy them. There are local apples everywhere, going to waste, but there’s no system for getting them to someone who might use them. We did ask a neighbor if they’d sell us some apples, and they said sure, they’d give us all we want. But those apples aren’t quite ripe.
On Friday at the Danbury farmer’s market, the farmer couple who I now refer to as our favorite farmers had some apples for 50 cents a pound. I bought enough for a pie. These apples look the way apples are supposed to look — all sorts of colors, with spots and even the occasional worm hole. No problem. Cut around it. To me, those perfectly shaped things in the grocery store that they call apples are not apples. They’re more like cardboard, usually.
The best apples I ever had were from old, abandoned apple trees.
A good persimmon year?
The wild persimmon crop won’t be ripe until early fall, but they’re coming along nicely. I pass three wild persimmon trees on the way to the mailbox, and they’re all heavily loaded with nice, plump, green persimmons.
I’m hoping for some nice persimmon pudding this fall.
Free building plans for farmers
The web site of North Dakota State University has a large set of free plans available online as PDFs. There are plans for houses, outbuildings, and all sorts of interesting devices such as solar dryers for fruit. Be sure to look through the miscellaneous category.
Speaking of roadside farm stands, I saw them all over the place on Maui, selling things like fresh fruit, or treats of some sort made on the spot. I wonder why we don’t have more of that sort of thing anymore around here. Back in the 1950s, when the family drove to the beach in the summer, I think we passed stands advertising “Ice Cold Watermelons” every few miles. One does occasionally pass someone selling produce off the back of a pickup truck.
Two books on Thomas Jefferson
As a Southerner (not to mention as an American) I have long been curious about Thomas Jefferson. The excellent HBO series on John Adams (available from Netflix) greatly increased my interest in Jefferson, and I resolved to read a bit about Jefferson as soon as I could get my hands on the right books. I asked an old boss of mine (thanks, Charlie) who loves that period of history for some recommendations. Ken Ilgunas recommended the same books, and Ken even picked them up for me at the Duke University library. They are:
American Sphinx: The Character of Thomas Jefferson, Joseph J. Ellis, Knopf, 1997
Twilight at Monticello: The Final Years of Thomas Jefferson, Alan Pell Crawford, Random House, 2008
Though, to my surprise, I think I would have agreed more often with Adams than with Jefferson on the political issues of the day, still Jefferson shines through these biographies as an incredibly nice man, an idealist, a product of the Enlightenment, a Southerner’s Southerner, an American’s American.
In the epilogue of Twilight at Monticello, there is an unexpected section on the decline of Virginia, and, along with Virginia, the decline of the South. This decline started around the time of Jefferson’s death. Southerners brought it on themselves:
“By the late 1840s, Virginia’s decline had become a matter of public comment, though little was done to arrest it. Before the Revolution, the Richmond Enquirer reported, Virginia ‘contained more wealth and a larger population than any other State of this Confederacy.’ By 1852, the Old Dominion, ‘from being first in wealth and political power, ranked below New York, Pennsylvania, Massachusetts and Ohio.’ These states, except for Massachusetts, were ‘literally chequered over with railroads and canals.’ …
“Intellectual life was almost nonexistent. Virginians published few newspapers and few books. Almost all literary works came from the North. The well-to-do refused to be taxed to pay for the education of their poorer neighbors, and the great majority of young people, white and black, received no formal schooling. A result was the almost complete absence of an educated middle class. There were only land-rich, cash-poor gentleman planters at the top, a somewhat larger group of lawyers, doctors, and merchants just below them, and then poor whites and free blacks at the bottom, followed by great numbers of slaves. Costly in itself, the presence of slaves discouraged the immigration of white laborers, denying Virginia much needed skills and enterprise.
“With discussions of slavery prohibited [by an act of the Virginia legislature], and the mails opened to confiscate abolitionist literature sent from the North, the entire society came to operate under censorship. Slavery, under increasing attack from the North, was passionately defended.”
By the time, about 110 years later, when I started becoming aware of the world, and the South, I’d been born into, not much had changed.
All work and no play: Not
Self-portrait: Ken Ilgunas in the Dan River
Quite a lot of work has gotten done at Acorn Abbey this summer. But Ken still has time to go on five-mile runs (2.5 miles each way) to the Dan River. There’s a swimming spot. Yesterday, Ken went on a hike in which he followed the little stream that crosses Acorn Abbey all the way to the river. Below are some of his photos from yesterday’s hike.